How to bypass registration on forums to view content
Saturday, 26 October 2013
Posted by
Unknown
Tag :
Windows
Requirements:
1. Mozilla Firefox
2. User Agent Switcher add on
3. Add On default user Setting
Steps to bypass registration on forums:
1. Use Mozilla Firefox for using this trick.
2. Now got to Tools tab in Mozilla Firefox and then select Add On.
3. Now download User Agent Switcher and Install It. Then it will ask for restarting web browser. Just restart your Firefox.
4. Now Go to Tools in Mozilla Firefox and then go to User Agent Switcher and select edit user agents.
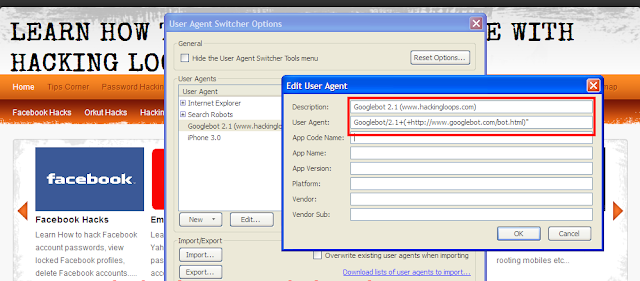
5. Now there Enter the Information carefully:
Then click on OK. Sample screenshot shown below:
6. Now close that and Again go to Tools in Firefox and then to User Agent Switcher and there select Googlebot 2.1(www.hackingloops.com).
7. You are done now. Now browse almost all forums without registration.
Drawback or Limitation:
Forums that has locked the bots from browsing their data cannot be bypassed using this hack. Also forums that uses noindex meta tag also cannot be bypassed using this trick.
1. Mozilla Firefox
2. User Agent Switcher add on
3. Add On default user Setting
Steps to bypass registration on forums:
1. Use Mozilla Firefox for using this trick.
2. Now got to Tools tab in Mozilla Firefox and then select Add On.
3. Now download User Agent Switcher and Install It. Then it will ask for restarting web browser. Just restart your Firefox.
4. Now Go to Tools in Mozilla Firefox and then go to User Agent Switcher and select edit user agents.
5. Now there Enter the Information carefully:
Description : Googlebot 2.1 (www.hackingloops.com)
User-Agent : Googlebot/2.1+(+http://www.googlebot.com/bot.html)"
6. Now close that and Again go to Tools in Firefox and then to User Agent Switcher and there select Googlebot 2.1(www.hackingloops.com).
7. You are done now. Now browse almost all forums without registration.
Drawback or Limitation:
Forums that has locked the bots from browsing their data cannot be bypassed using this hack. Also forums that uses noindex meta tag also cannot be bypassed using this trick.
Commands in Demand , All useful Windows commands, settings on 1 click
Friday, 25 October 2013
Posted by
Unknown
Tag :
Windows
Commands in Demand provides non-technical users with easy access to
more than 150 Windows commands and features that can be hard to find or
time consuming to get to. The program includes shortcuts to terminate
non-responsive applications, restart Windows Explorer, view/clear the
clipboard, open a command prompt in a selected folder, access system
folders, view TCP/IP configuration settings, etc.
It has a selections menu (sections) according to were its commands
are related. If a command is related with more than one section and in
order to be less confused, you may find the same command buttons more
than one times.
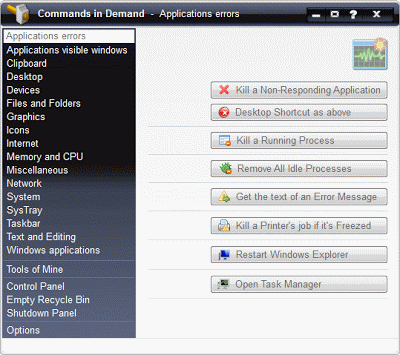 |
Here are some of the commands that are available in your demand:
» Applications’ Shortcuts creator to minimize apps in the SysTray
» Clipboard real-time Editing
» Color Sample Picker
» Command Prompt starter in any folder of the System
» Desktop Icons Refreshing
» Desktop Shortcuts Copy to a desirable folder
» Device Manager with Hidden Devices
» Hide / Show Desktop Icons
» Icons Extraction from files
» Images Conversion of known formats
» Internet Searching with Two Engines simultaneously
» List Alphabetizer Application
» Memory and CPU Info
» Memory Instantly Cleaning
» Non-Responding Applications Killing
» Running Processes Killing
» Safely Removal of USB Drives
» Screenshots of whatever is visible
» System Drives Quick Cleaning
» System instant General Refresh
» System’s Clock Hiding
» System’s Volume Mute
» Taskbar Hiding
» Transparency Level to the Active window
» Transparency Level to the Taskbar
» URL Shortcuts creation
» User’s and Common System Folders browsing
» Windows commonly used and hidden applications starter
» WinLogoKey shortcuts simulator
Hey Guys,Today I am going to tell you about "How to create a Autorun.inf file for USB drives or simply CD drives"
so that it can execute programs. Programs can be viruses, keyloggers,
rats or simply normal services that you want to execute automatically
whenever user open his/her pendrive or USB drive. Its the easiest way to
spread your programs to schedule, so that they can execute by itself
without any user interaction.
Creating a simple or complex autorun file for your pendrive or USB drive.
Note: You can also follow these instructions when making a CD. You just have to burn it on the cd.

When
you plug a USB or pen drive in, you might be interested in making a
program, or other things happen as soon as you plug in. The way you
accomplish this is through the Autorun.inf file. The autorun.inf file is
located in the root of the usb drive and tells Windows what to do
automatically.
This autorun can be used for good things and also for bad things depending on what you like. I am Destructive Mind, so i use it to run my coded viruses and keyloggers to execute automatically by themselves as soon as user open folder or simply opens pen drive or usb drive.
This tutorial covers:
This autorun can be used for good things and also for bad things depending on what you like. I am Destructive Mind, so i use it to run my coded viruses and keyloggers to execute automatically by themselves as soon as user open folder or simply opens pen drive or usb drive.
This tutorial covers:
- Creating a USB Autorun.inf
- Changing label\icon of thumbdrive
- Making a new option appear in the autorun menu
- Making programs automatically run when plugged in
So Read On How to create Autorun.inf file...
Creating a USB Autorun.inf :
To
create an autorun file, open Notepad and save ‘autorun.inf’’ (with
quotes) and save it to the root of the drive. All it needs to have is in
the first line;
[autorun]
[autorun]
Changing label\icon of thumbdrive:
Follow the steps in Creating a USB Autorun.inf. Before you save it, type this in in this order!
[autorun]
icon=myicon.ico
label=MyLabel
And save. Make sure the icon file is in the root of your drive.
[autorun]
icon=myicon.ico
label=MyLabel
And save. Make sure the icon file is in the root of your drive.
Making a new option appear in the autorun menu:
Right, so make your autorun file and type this into Notepad:
[autorun]
icon=default
label=[yourlabelhere]
action=programname.exe
Save it and exit. Once again, the program has to be in the root. Now, when you plug it in, the option should appear in the menu.
[autorun]
icon=default
label=[yourlabelhere]
action=programname.exe
Open Program
Save it and exit. Once again, the program has to be in the root. Now, when you plug it in, the option should appear in the menu.
Making programs automatically run when the USB is plugged in:
Follow the same instructions
[autorun]
Icon=default
label=YourLabelHere
open=programname.exe
[autorun]
Icon=default
label=YourLabelHere
open=programname.exe
And that’s it for this tutorial! Your Autorun program is ready to execute whatever you want. Here i have written to execute a simple program called programname.exe
You must have come across Threads relating Hacking Social Networks Sites. You must now Know that These sites cant be Hacked as it has the MOST ADVANCED SECURITY PATCHES in it!! But one can steal the password of Users involved in the respective Sites!! So lets come across the Types Of Stealing in Social Networking World :
1) Phishing : This is a very ancient method of hacking passwords. Just one need to create a fake login page and send it to the victim as mail but secretly.It generally says that “we are moving our database,so we need to verify the users” or “You just win a lottery, please verify yourself”. As the victim enters the username and password ; it will be directed to the hacker’s destination.
Preventions: Don’t login to the pages you are not Familiar with!! Your friends or scammers may send you Those Fake LOGIN PAGE by making some Attractive offers!! Don’t try the pages which redirects you to the Fake login Page!! To login to any sites use their original addresses: e.g.for Facebook Type “www.facebook.com” don’t login through any other Links !!
2) Socail Engineering : The best way to hack someone whom you know very well!! Its done by answering the secret Questions : the alternative way to access to your accounts!! The hackers go to the Forgot password option, answer the security question then change the password from there!!
Prevention: Its very easy . Use the secret question anywhere from your own:its fully your own(personal).Don’t share it. Don’t use the predefined questions as stated by the sites !!!
3) Keylogging, Istealer: These are the most dangerous spyware!! It not only steals ur Social Network password but steal everything n every detail of your networking history!! Here the hacker told you about some attractive offer or something what you want. If you download the application, it also contains the said keylogger software attached.It will send all your details of your networking history to the hacker’s destination !!
3) Keylogging, Istealer: These are the most dangerous spyware!! It not only steals ur Social Network password but steal everything n every detail of your networking history!! Here the hacker told you about some attractive offer or something what you want. If you download the application, it also contains the said keylogger software attached.It will send all your details of your networking history to the hacker’s destination !!
Prevention: 1) keep the latest and verified antivirus and security features updated!!
2) Don’t download softwares and files from Untrusted sites or source!!
These are some basic security tips!! If u follow these properly, Your account is almost 90% safe from Hackers……
Please share this, if you liked it.
In the present world of high-speed internet, people have grown curiosity towards HACKING. Everybody is searching for a secret passage or method to bypass, extract, get and modify the information by any means. Among teenagers, the general tendency of hacking is concentrated to social media accounts.
Here I will describe all the methods which are popular in the world of hacking in order to hack into a computer terminal and online account.
1. Phishing
This is a method where you have to bring the user to a webpage created by you which appears to be the same as the interface of the legitimate one and get him/her to enter the credentials. Then the redirect page will land somewhere else and you will get the password in your mail box as defined inside the php script.
2. Keylogger
Consider a situation; everything you type in the system is mailed to the hacker! Wouldn’t it be easy to track your password from that? Keyloggers perform similar functionalities. So you have to be cautious while typing anything. Now a day, remote keyloggers are also used. So before downloading any executable file keep an eye on the downloadable element. Also lookout for your open ports… someone might be looking into it. Periodically check “netstat” from command prompt.
3. BruteForcing
This is quite a long and most tiring task. This method is very useful if you know that the victim is using his password among a few known possibilities that you are aware of. If you don’t know much and the possibilities are more, then you shouldn’t go for it.
4. Secret Question
According to a survey done by security companies, it is found that people generally complain for hacking as per their secret question answers. This is indeed a much easier method. In some cases, there are only fixed secret questions, so it becomes much easier for the hackers. So, don’t use simple answers, don’t reveal it to anyone and I would suggest you to use own secret questions with answers.
5. Social Engineering
This is one of the oldest tricks to hack. Try to convince the user that you are a legitimate person from the system or central server and needs your password for the continuation of the service or some maintenance or you need to reset your password to some combination like ‘abc12345’. This won’t work now since most of the users are now aware about the Scam. But this Social Engineering concept is must for you to convince the victim for many reasons. It may work in some case.
6. Fake Messengers
This is a form of phishing in the application format. Sometimes, there are some fake applications which tend the user to enter the login info in the software and check your mail. But unknowingly, your login credentials are being sent to the ftp server destination of the hacker.
7. Viruses And Worms
Viruses and worms are self-replicating programs or code fragments that attach themselves to other programs (viruses) or machines (worms). Both viruses and worms attempt to shut down networks by flooding them with massive amounts of bogus traffic, usually through e-mail. So install a good working antivirus and antispam program which is capable of handling the potential threats.
8. Back Doors
Hackers can gain access to a network by exploiting back doors administrative shortcuts, configuration errors, easily deciphered passwords, and unsecured dial-ups. With the aid of computerized searchers (bots), hackers can probably find any weakness in the network. So you have to strengthen your security to avoid unauthorized access.
9. Trojan Horses
Trojan horses, which are attached to other programs, are the leading cause of all break-ins. When a user downloads and activates a Trojan horse, the software can take the full control over the system and you can remotely control the whole system. Isn’t it great! They are also referred as RATs (Remote Administration tools). Always periodically watch out your open terminals by checking ‘netstat’.
10. Denial Of Service
DoS attacks give hackers a way to bring down a network without gaining internal access. DoS attacks work by flooding the access routers with bogus traffic (which can be e-mail or Transmission Control Protocol, TCP, packets).
11. Distributed DoSs
Distributed DoSs (DDoSs) are coordinated DoS attacks from multiple sources. A DDoS is more difficult to block because it uses multiple, changing, source IP addresses. So better to use upgraded and advanced servers like grid server etc.
12. Sniffing
Sniffing refers to the act of intercepting TCP packets. This interception can happen through simple monitoring or something more wicked. So it’s better to secure the working network. Also make sure that, none of your users is giving your TCP packets to outer network knowingly or unknowingly. Knowing IP address only also can do a lot as there is a powerful penetration tool to do the damage (BACKTRACK OS + METASPLOIT).
13. Spoofing
Spoofing is the act of sending an illegitimate packet with an expected acknowledgment (ACK), which a hacker can guess, predict, or obtain by snooping.
14. SQL Injection
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. It uses normal SQL commands to get into database with elevated privileges. Some security precautions need to be taken to handle this attack.
15. Cookie Stealer
Each time you access into an online account, the sites identify your system and you by your cookies. If somebody gets the cookie saved by the sites, then he can easily decode it and can get the password! This is generally possible in open networks. So while using open networks always use https as it makes you enter into secure mode without leaving the cookie to the network.
16. DNS Poisoning Or PHARMING
Phishing is a tough job. Isn’t it? Convincing someone to enter their password at your page require a lot mind work. What if you don’t have to convince the person? What if they are directed automatically to your site without having a clue? DNS poising or Pharming does the same for you.
For details on DNS poisoning –click here
17. Whaling
This method gets you the password of the accounts which are used by the hackers to receive the passwords. So you just have to hack one ID, which is simplest method and you will have loads of passwords and so loads of accounts at your mercy..!!!